
Detect and respond to insider risk
What makes Incydr different
Incydr is a SaaS data risk detection and response product that allows security teams to effectively mitigate file exposure and exfiltration risks without disrupting legitimate collaboration.
Quickly uncover your data security blindspots
Incydr detects file exposure and exfiltration across computers, cloud and email through an agent and direct integrations. It monitors all file activity (creation, deletion, modification and movement) regardless of what is considered acceptable or unacceptable by security policy. This comprehensive approach to monitoring reduces deployment and management time by removing the rule creation and refinement process. It also illuminates an organization’s data security blindspots by showing activities that fly under the radar of other security technologies. You’ll get an accurate understanding of your insider threat vulnerabilities.
Cut through the noise to find real risk
Incydr is smart enough to know there’s a difference between everyday collaboration and the events that represent real risk. It filters out the noise of harmless activity, like sharing files between trusted domains, to reveal only the threats that could harm your business. Incydr takes a multidimensional approach to insider risk by combining rich context on files, vectors and users. It surfaces this information along with additional risk indicators to prioritize the events that require immediate security investigation.
Speed
Take a right-sized approach to insider threat response
Incydr provides the fast answers needed to substantiate insider threat investigations. There’s no one-size-fits-all to insider threat response. Response actions should vary based on impact, employee history and intent. Armed with the facts, your organization can take a right-sized response. Whether that be automated action, corrective conversation, additional training or even legal action.
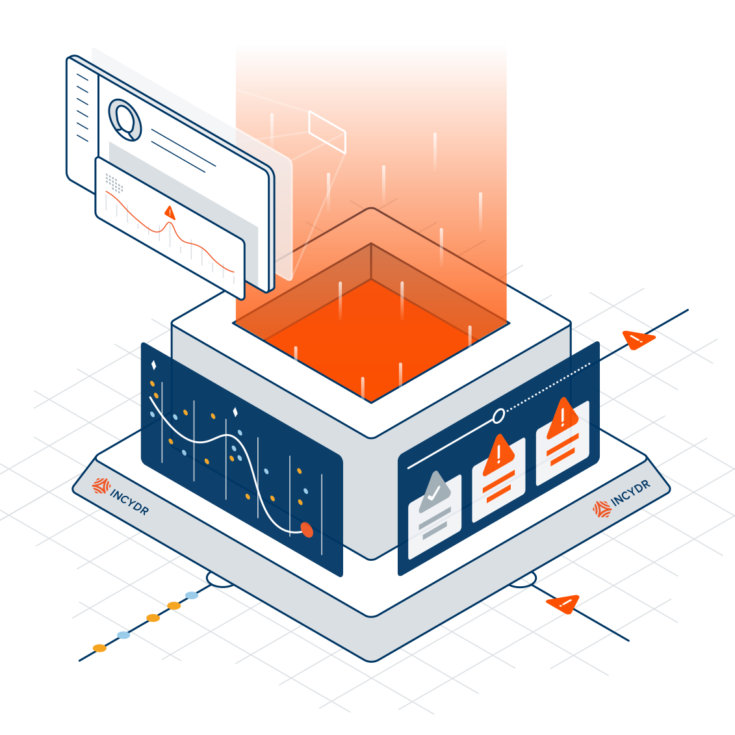
How Incydr Protects Business Data
3 Dimensions to Insider Risk: Files, Vectors and Users
Incydr allows you to detect and respond to data risk caused by those inside your organization. This includes exposure and exfiltration activities on computers and via corporate cloud and email services.
The foundation of Incydr’s ability to speed insider risk detection and response comes from monitoring all file activity regardless of what is considered acceptable or unacceptable by security policy. Incydr logs every file event and enriches it with context on the vector, file and user to determine what represents real risk. This allows Incydr to not only reduce alerts and investigation time, but also remediate risk that goes unnoticed by traditional data security technologies.
File
- Monitors all files – not just those that have been deemed sensitive
- Offers critical metadata including file name, owner, size, path, category and hash
- Provides authorized security analysts with the ability to review the file’s actual content
Vector
- Detects exposure and exfiltration including web browser uploads, cloud sync activity, file sharing, Airdrop, and use of removable media
- Offers vector detail such as domain name, active browser tab title and URL, and removable media make, model, volume name, partition ID and serial number
- Filters file events to reflect what is considered trusted vs untrusted activity

User
- Identifies behavioral risk indicators such as remote activity, off-hour file events and attempts to conceal exfiltration
- Allows security teams to programmatically monitor users with increased risk factors, such as departing and contract employees
- Provides 90 days of historical user activity to surface trends and abnormalities
Curious about this product?